
By:
Eric De Grasse
Chief Technology Officer
The Project Counsel Group
Gregory Bufithis
Founder, CEO
The Project Counsel Group
16 July 2018 (Paris, France) – Last month the EMEA Unit of the international insurance group AIG issued its much-followed annual cyber claims statistics report (this one for 2017) and has conducted several related webinars detailing the report. The report reflected both the growing maturity of the cyber book of business and a threat environment which has, in the last 6-9 months, been characterized by a series of sophisticated, systemic malware and ransomware attacks, including WannaCry and NotPetya. While business/network interruption was a significant issue for many European organisations, the majority of these losses were underinsured.
Methodology: in March 2018, AIG Europe carried out an analysis of more than 600 claims notified under its cyber policies between 2013 and December 2017.
It is an extremely detailed report with scores of graphs and tables so we cannot cover all of it. The following will be highlights (and yes, it is still a long read) but among the more interesting observations:
- ransomware has become commoditized making attacks even easier
- professional services continue to be a preferred target for data theft
- the GDPR (General Data Protection Regulation) tops the list of data breach trends, and may lead to more cybercrime.
As had been predicted early last year by AIG’s cyber experts, 2017 was a year of widespread ransomware attacks and cyber business interruption. AIG’s claims statistics show that over a quarter of cyber claims (26%) received in 2017 had ransomware as the primary cause of loss. This is a significant leap from 16% of claims in the years 2013-2016. From the webinar (all further quotes are also from the webinar):
The combination of leaked National Security Agency (NSA) tools plus state-sponsored capabilities triggered a systemic event. The Wannacry outbreak, which hit hundreds of thousands of machines around the world, could have been worse in terms of scale and insured losses if a UK researcher hadn’t quickly found and activated the kill switch.
After ransomware, data breach by hackers, other security failure/ unauthorized access and impersonation fraud were the other main breach types. While the proportion of claims caused by employee negligence reduced marginally to 7% in 2017, human error continues to be a significant factor in the majority of cyber claims.
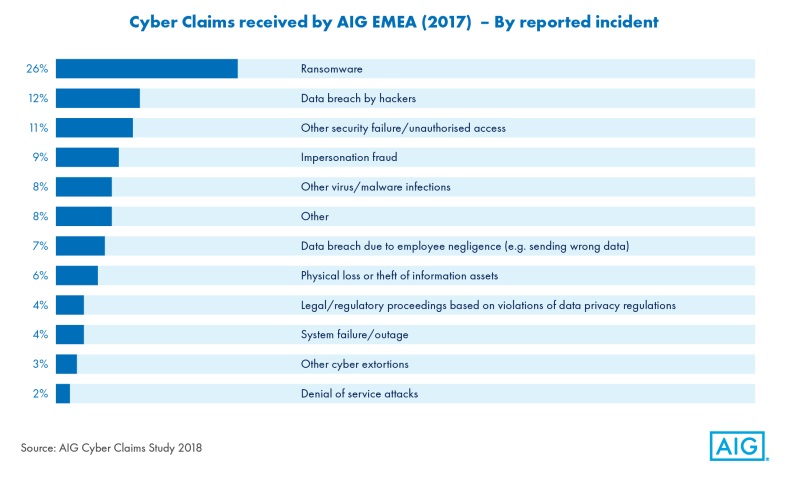
Claims frequency has also increased yet again in the last year. In 2017 AIG’s specialist cyber claims staff were handling the equivalent of one claim per working day. The growth in claims frequency reflects a broader trend of cyber loss escalation. As cyber insurance becomes a more common purchase for many organizations, buyers are also becoming more familiar with the product. They understand more fully the scope of their cover and what incidents can and should be notified to their insurance carrier. Take-up of cyber insurance grew substantially in the wake of a wave of systemic ransomware and distributed denial of service (DDoS) attacks. This in itself is likely to contribute to greater claims frequency going forward:
We’re seeing a lot more interest now from non-traditional buyers of cyber insurance, so can expect an increase year-over-year in the number of claims, just based on the growth of the premium.
A threat for all industry sectors
AIG’s claims statistics reflect the fact that no sector is immune to cyber attack. In 2017, cyber claims notifications were made by insureds in eight sectors that had previously not featured at all in AIG’s cyber claims statistics. This is a continuing trend, whereby a larger number of notifications each year are coming from an increasingly broader range of industry sectors, such as energy and transportation, and not just those traditionally associated with cyber risk.
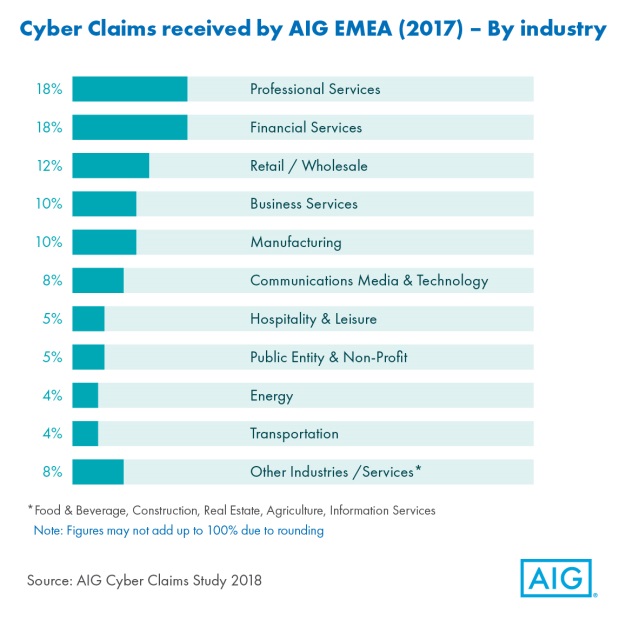
While financial services continues to be a major contributor of claims, the sector made up a lower percentage in 2017 (down to 18% compared to 23% in the years 2013-2016). The very nature of the business of banking and insurance, the fact that financial institutions (FIs) collect and store vast amounts of data and are subject to stringent regulation (and potentially steep fines), has meant that financial services firms have always needed a robust approach to cyber risk.
However, the reduction in the proportion of claims coming from FIs could simply reflect the steady growth in claims from other industry sectors, as a result of the growing maturity of AIG EMEA’s cyber book of business:
Historically the financial services segment has always been one of the biggest segments for us, but since last year we started to see a lot of other industries taking out our coverage. This was particularly driven by the events over the summer.
Many of the recent ransomware attacks have been indiscriminate in terms of which industry they hit. If the users of the software that’s being targeted have a particular vulnerability they are going to get impacted by these blanket attacks that we saw a lot of in 2017. But it will be interesting to see if we get more targeted attacks in 2018, particularly with the current political environment ripe for state-sponsored activity.
More importantly:
Professional services saw a significant increase in its proportion of overall claims (up to 18% from 6% in 2013-2016), while other sectors more commonly associated with cyber claims saw their shares decrease. Professional services have become more of a target for data theft. Certainly solicitors and lawyers and accountants with large databases of clients are attractive to cyber-criminals because of the quality of the data they hold, and are vulnerable to cybercrimes that target regular financial transactions.
And if you attend any off the plethora of cyber conferences you still hear this attitude from company leaders: “it won’t happen to me” or “I don’t have any interesting data so why would I be a target?” But even if a business doesn’t hold interesting data it can still fall victim to ransomware extortion, and if files are encrypted the business cannot function. That is the trend.
Ransomware becomes commoditized
Major systemic events impacted organizations in many European countries last year. WannaCry targeted a Windows vulnerability that was used to spread malware to hundreds of thousands of machines in over 150 countries. It impacted companies in numerous sectors, including healthcare, financial services, logistics, education and manufacturing.
Over the past 24 months ransomware has become increasingly commoditized with the creators of more recent variants offering revenue-sharing agreements to “affiliate partners”. There is no longer a guarantee that insureds will get their data back, even if they pay the ransom. The “professionalism” associated with earlier strains of ransomware – where call centres were provided to talk victims through accessing Bitcoins in order to pay the ransom and get their data restored – has now all but gone.
However, Ransomware-as-a-Service still poses a threat to organizations. Companies may not think their data is important or likely to be compromised, but the claims experience in 2017 demonstrated that ransomware attacks are largely indiscriminate and can impact organizations from all sectors and of all sizes. AIG anticipates that the automation and commoditization of ransomware will continue to be a trend with businesses and individuals facing an increasing number of attackers.
There is also an expected shift in emphasis towards crypto jacking.
NOTE: for a good article on crypto jacking and crypto mining we recommend this piece by Jason Bloomberg: click here
Over the course of 2017, the crypto market appreciated more than 1,200%. But the increase in the value of electronic currencies has drawn the attention of cybercriminals, who are increasingly taking over networks and using malware to mine for cryptocurrency.
Looking ahead, the more traditional forms of extortion are expected to become an issue in data breaches and become more targeted. This is currently a trend in the U.S. market but has also resulted in losses for European companies, particularly those with a US presence. The EU General Data Protection Regulations (GDPR) is likely to become another tool for negotiation by extortionists, who will threaten to compromise an organization’s data unless a payment is received, knowing that the consequences will be more significant under the new regime.
GDPR tops list of data breach trends
A surge in data breach and other security failure claims was expected after the GDPR came into force on 25 May 2018. Companies will be more inclined to report breaches, with the impact on cyber claims similar to that witnessed in the U.S. after state breach notification laws came into effect:
A lot of smaller insureds had received advice that they should make a notification but they’re not obliged to under the old statute. But that’s not going to be an option for them with the GDPR. So we’re certainly anticipating more notifications after that.
One AIG analyst noted there has been a shift in attitudes towards personal data since the Cambridge Analytica and Facebook personal data scandal story broke and expects this could impact the type of claims received in 2018, with consumers being significantly less accepting of their personal data being breached than they were in the past:
We recently dealt with a claim following a breach at a university. They made the notification as if GDPR was already in place. That proved to be quite a costly exercise and it was also difficult for them to manage reputationally. When you notify 100,000 people that can snowball into quite a big undertaking. Individuals can be quite upset when they get these data breach notification letters, even if they are precautionary.
We should note here that the outcome of the collective action in the UK courts against the supermarket giant Morrisons, filed by staff, will be an important test case on how courts are likely to compensate those whose data has been compromised. The employees are seeking compensation for the “upset and distress” caused after the personal data of nearly 100,000 staff was stolen in 2014. (The court granted Morrisons leave to appeal his ruling so that a higher court could consider it).
There is some anticipation the introduction of GDPR could see more shareholder lawsuits against companies and their directors in the future. The U.S. has had strict notification requirements for a number of years and nearly every high-profile cyber breach is met with at least one class action lawsuit.
NOTE: while the same level of litigiousness and collective redress mechanisms do not yet exist in Europe, the Morrisons ruling could pave the way for similar actions to be brought in the future. If in the case of Morrisons there is an award or damages based on the emotional distress caused by the loss of data, that could be significant and set an interesting precedent. It could fuel more of these types of actions against organizations once they have notified the public of a breach.
Interesting points raised during the webinar:
Most directors and officers (D&O) policies are not going to have an exclusion for shareholder legal action brought following a cyber breach, so they are going to respond in light of those types of claims. There is currently quite a lot of uncertainty regarding the GDPR because there’s also the element of the fines and penalties. This could be the first year that we start seeing some of those things coming to light, depending upon how aggressive regulators choose to be with the new laws.
But our chats with the regulators indicate that most think they need at least one year to figure out the regulation themselves. And as we indicated in one of our GDPR webinars, the negotiations tore out the “connective tissue” of much of the regulation so opaqueness abounds. And the overlapping ePrivacy Directive (with all of its contradictions to the GDPR) will not make it any easier.
And one large fear: cyber-criminals will not see the regulation as any sort of deterrent. The value of personal data of companies is greater than ever before. Extortioners are in a stronger position in their negotiations if they threaten to publish the data of an organization, a prediction made by AIG. So a company may be quick to pay a ransom and then need to deal with reporting the breach. Or just pay the ransom and shut up:
If successful attacks do take place however, cyber-criminals may be able to demand high ransoms due to the fines that can be given by authorities for a breach.
And in a note above we mentioned the traditional Denial of Service (DoS) attacks that can flood your system. But what if someone deliberately floods your business with GDPR requests? Cyber experts have coined a new attack … GDPR Denial of Service (GDoS) … that could bury your staff for months answering GDPR requests. AIG suggested just what such an access might look like:
It’s all perfectly legal – making it the ideal protest weapon for hackers and anarchists alike. But GDoS doesn’t stop there. For example, a state-sponsored hacker seeking to cause as much disruption as possible, could try and use a country’s infrastructure against itself.
First the hacker could create a large target list of vulnerable businesses (hotels, schools, gyms, restaurants, lawyers, etc.). Next, they would hack these systems, steal and publish their data as widely as possible forcing the DPC to audit and penalize the organizations. Finally, they’d go back and do it all over again. Like a Food Safety Authority inspector closing an unsafe restaurant, the DPC would have little choice but to suspend processing if a business is repeatedly hacked. If an attack is properly targeted it’s possible an entire geographic region could be shut down as effectively as with traditional weapons.
Sadly, this isn’t so unrealistic. If you read the joint cyber notice last year issued by the UK’s National Cyber Security Centre and the FBI/U.S. Department of Homeland Security “Russia is gathering intelligence to potentially lay a foundation for future offensive operations on the regulation front”.
But a GDPR Denial of Service attack isn’t limited to state-sponsored hackers. Protesters, hacktivists, trade unionists and civil disobedience of any colour have a new, legal and very powerful tool at their disposal. While organizations can ignore an individual who submits 1,000 GDPR access requests, they cannot ignore 1,000 individuals each submitting an access request, or those who object to the organization processing their data. It could take an organization months to clear the backlog while costing a small fortune and completely disrupting day-to-day operations.
Disgruntled employees on social media could orchestrate wildcat GDoS protests as a powerful alternative to striking, all without losing a single day’s pay. Animal rights movements famous for creative protests could launch costly and disruptive campaigns targeting businesses with a single click of a mouse. Similar for human rights activists.
Ah, the GDPR: be careful what you wish for.
