
25 July 2015 – The emerging consensus view of humanity’s imminent future is that just about everything will soon be interconnected with just about everything else. In a recent report on Digital Life in 2025, the Pew Internet Project predicted that the internet would soon become a “global, immersive, invisible, ambient networked computing environment built through the continued proliferation of smart sensors, cameras, software, databases, and massive data centers in a world-spanning information fabric known as the Internet of Things.”
Like big data and the smart grid, the Internet of Things (IoT) concept has become a buzz word in the technology trade press. The IoT is predicted by many technology experts to be as – if not more – transformational than the internet itself on the way we live.
Except many folks seem to forget about the cyber hackers and about über-connectivity system failure.
The big cyber news this past week was that Fiat Chrysler has recalled 1.4 million vehicles over a vulnerability that could allow hackers to disable them on highways, highlighting the risks facing automakers as they connect car systems ever closer to the wider world. The carmaker’s action … the first recall in the U.S. over concerns about hacking … covers a series of vehicles from the carmaker’s Chrysler, Dodge, Jeep and Ram brands.
It follows an article published on Tuesday in Wired magazine detailing how hackers were able to use the radio of a Jeep Cherokee sport utility vehicle, one of Fiat Chrysler best-selling models, to disable its transmission as it drove down a public highway near St Louis.
And if you’ve covered our previous reporting these hacking issues are somewhat old news. The Federal intelligence authorities have been quite concerned for a number of years about cyberattacks on the electronic control units (ECUs) in modern cars and other modes of transport. These ECUs represent the brains of most modern cars. The death of Rolling Stone investigative journalist Michael Hastings three years ago is believed to have been caused by such an attack.
Note: when the Wired magazine article broke we were in Zurich at a complex networks symposium. The Wired article created quite a buzz. We had just finished discussing last week’s “systems events”, United Airlines grounding of nearly 5,000 flights when its computer system crashed, and the computer glitch that halted trading on the New York Stock Exchange for over three hours. Some saw the sinister hand of a hacker in these outages, but as the presenters stated these were far more likely to be a coincidence, an intrinsic feature of the system rather than a bug. Our networks will go down all the time now, a consequence of unprecedented levels of interconnection. Disruptions can occur even in the most robust networks, whether these are power grids, global financial markets, or your favorite social network. As Alexis Madrigalhas observed “when things work in new ways, they break in new ways.” The purpose of the symposium was to provide a fresh new understanding of such systems — the way they grow, and how they break — so that the legal professionals and IT professionals in attendance can better understand this new environment and advise their clients.
The Wired magazine experiment was troubling because the hackers previously believed an attack on the Cherokee would be possible only over a direct WiFi from yards away. The actual attack occurred at a distance of 10 miles, and involved a wide range of safety-critical vehicle systems.
The recall comes with carmakers under growing pressure to integrate their vehicles with modern communications technology, partially because of the popularity of smart devices among younger buyers who are less enthusiastic about cars than their older peers.
Fiat Chrysler has been all over the media stressing that the hackers had required “unique and extensive” technical knowledge to undertake the Wired stunt, as well as prolonged physical access to a vehicle and extended periods to write code. In one press release:
“The company is unaware of any injuries related to software exploitation, nor is it aware of any related complaints, warranty claims or accidents, independent of the media demonstration.”
The take by most analysts was that the Wired magazine stunt will make carmakers much more aware of and concerned about their susceptibility to hacking. And as we discussed at the symposium, when you have this level of connected car technology and there has already been a major vulnerability shown up, it shows it’s a difficult problem. It is simply not unrealistic to regard vehicles’ electronic control systems, to which the hackers gained access, as of similar importance in terms of safety to a vehicle’s brakes or fuel system. The industry is going to need a fresh pair of eyes from a security perspective. Something they are not used to doing.
And the hacking vulnerability is likely to increase the scrutiny of connected car technologies by the U.S. National Highway Traffic Safety Administration. The agency has already expressed serious misgivings about the potential for drivers of connected cars to be more distracted, a significant factor in the nearly 33,000 annual US road deaths.
Interesting point by Charlie Miller, one of the security experts who was involved in the Chrysler Jeep hack:
“If you can hack into my head unit and make my brakes not work, then that’s a different story. Let’s stop the attack after they’re already in. If you hack into my car’s head unit and change the radio station, I don’t care. I can live with that.”
The point: instead of building firewalls to keep cyber attacks out (which our cyber guys tell me is ultimately a futile endeavor), build systems that recognize what a security breach looks like in order to stop it before any real damage is done.
If you have worked in cyber security, you recognize the strategy. It’s called operational security, and the auto industry — even the banking industry — has been slow to adopt it. They assume hackers can’t get through their perimeter security, which is not true. That’s a basic principle for security.
What the Wired article showed was that you could hack through the perimeter security and into the Jeep’s UConnect head unit, also known as an infotainment system. Previously, hackers could breach a vehicle’s internal computer bus only by physically connecting to a car’s onboard diagnostics (OBD-II) port. The hacker’s demonstrated that by using the vehicle’s cellular network connection, they could wirelessly talk to the Jeep’s head unit, and then access the Jeep’s control area network (CAN).
IHS Automotive published a nifty graphic:
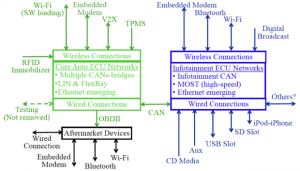
Diagram shows more than a dozen wireless access points to a vehicle’s head unit
and controller area network (CAN).
Lucas Mearian of ComputerWorld explained it as follows:
“All modern vehicles have a CAN, which acts as a computer superhighway to the vehicle’s various electronically controlled components. Once on the CAN, Miller and Valasek discovered which electronic messages controlled various systems, and they were able to send messages to remotely control the brakes, transmission, acceleration and other vital components.
As cars become more connected to other vehicles, surrounding infrastructure and to manufacturers and their parts suppliers, the ability to breach a vehicle’s security will only become easier.
And, as autonomous functionality — even fully self-driving cars — emerge, it will mean that protecting computer systems from attack will become more crucial.
At the same time, car makers already remotely collect data from their vehicles, unbeknownst to most car owners, in order to alert the drivers to needed repairs or maintenance and for future research and development.”
And therein lies the issue I have written about countless times before: consumers don’t know with whom that data is being shared. As Nate Cardozo (an attorney with the Electronic Frontier Foundation and Twitter chum) has pointed out as an example, the Ford Sync, in its terms of service, says it’s collecting location data and call data if you use Sync to dictate emails. Sync is Ford’s current Microsoft Windows-based telematics or head unit system. The company is changing over to a QNX-software based system this year.
And as I have learned at such events such as the Mobile World Congress and Black Hat, while Chrysler might fix this specific remote flaw, there are probably many others yet to be exploited. I don’t think there’s a method to make a really secure way for computers to communicate. Hacking a network firewall simply takes time and perseverance. Once past a firewall, hackers can make computers imitate any other computer on a network, and that means they can control the systems through electronic messaging.
This is not to say a more secure method, such as using cryptography or encrypted messaging within a vehicle’s CAN, could make it more difficult to hack. But, if an attacker has physical access to a car, they can get access to the firmware on various computer chips and figure out what the encryption keys are. Every car isn’t going to have a different key. Once one car is hacked, all the models are vulnerable.
Carmakers are far behind the security curve, not only because vehicles have an average six-year development cycle, but also because they haven’t taken the potential security problem seriously. Over the last 3 years at the Mobile World Congress I have seen the “connected car” space growing and growing. And I heard how communications and entertainment systems feature different architectures, that vehicles have a hardware based built-in firewall that separates the vehicle control network from the communications and entertainment network. And then the manufacturer express “shock and surprise” when the systems cannot detect errant messages that could indicate a cyber security breach has occurred — and then shut the car down.
And the marketing pressure, the enormous effort by automakers to create the “connected car”, web-linked cars that are the next digital frontier and key to the auto industry’s efforts to attract younger, tech-savvy car buyers, which is more than just about accessing email or Twitter. Connected cars will be able to help drivers navigate the best route home at rush hour, automatically schedule maintenance appointments and even order and pay for takeout food. The business opportunity is enormous for both automakers and mobile operators and encryption and “interception prevention and alteration” are on the back-burner.
It is why the cyber guys say car companies could “easily” build a separate computer to detect errant messages. The computer would watch the messages that flow between a vehicle’s computers or electronic control units and use a database to determine which messages are authentic. One of the best I have seen was at the DLD Tel Aviv Innovation Festival, Israel-based Argus Cyber Security which is a start-up that sells detection software for the connected car industry. Argus’s Deep Packet Inspection algorithm scans all traffic in a vehicle’s network, identifies abnormal transmissions and enables real-time response to threats.
Or the layered approach to security. Hardware-based encryption with cyber attack detection is the most promising for securing the future of the connected automobile.
Or Symantec’s idea of digital certificates — a “digital handshake” so to speak between computer systems — as the key to providing privacy while also allowing crucial driving data to be gathered. The data will help local governments and auto manufacturers improve overall traffic conditions; the individual driving experience can use data that comes from a vehicle’s internal computers.
Modern vehicles can have as many as 200 electronic control units and multiple communications networks between internal computer systems. While most systems are isolated within the car, others are used to transmit data back to manufacturers, dealers or even the government. On the plus side, this data can make the user experience much richer and personalized because from one vehicle to the next, it will know all my settings and be able to integrate your car into your digital day. The flip side of that is it creates risk.
But it’s all about coffee.
As we learned in Zurich last week, researchers usually think of network connectivity as happening in a slow, continuous manner, similar to the way water moves through freshly ground coffee beans, slowly saturating all the granules to become coffee in the container below. However, over the past few years, researchers have discovered that in special cases, connectivity might emerge with a bang, not a whimper, via a phenomenon they have dubbed “explosive percolation.” This new understanding of how über-connectivity emerges is the first step toward identifying warning signs that may occur when such systems go awry – for example, when power grids begin to fail, or when an infectious disease starts to mushroom into a global pandemic. Explosive percolation may help create effective intervention strategies to control that behavior and, perhaps, avoid catastrophic consequences.
The formation of connectivity can be understood as a phase transition, the process whereby water freezes into ice or boils away into vapor. Quoting Raissa D’Souza, a physicist at the University of California, who has done some fascinating work on über-connectivity, large, complex networks and cyber security:
“Phase transitions are ubiquitous in nature, and they also provide a handy model for how individual nodes in a random network gradually link together, one by one, via short-range connections over time. When the number of connections reaches a critical threshold, a phase shift causes the largest cluster of nodes to grow rapidly, and über-connectivity results. Seen this way, the percolation process that gives rise to your morning cup of joe is an example of a phase transition. Hot water passes through roasted beans and shifts into a new state – coffee.”
All of this connectivity is a double-edged sword. For normal operating systems like the Internet, airline networks or the stock exchange or even our cars, we want them to be heavily connected. But when we think about epidemics spreading, or a cyber attack, we want to curtail the extent of the connectivity. Even when high connectivity is desirable, it can sometimes backfire, causing a potentially catastrophic collapse of the system.
So this “explosive percolation” is a first step in thinking about control because it provides a means of manipulating the onset of long-range connectivity via small-scale interactions. It is why cyber experts are applying it so when a collapse or an attack occurs this patchwork approach could be used to reverse the process, breaking up the über-connected system into a collection of disjointed clusters, or “islands,” to avoid catastrophic cascading failures or attacks.
A topic to be explored in more depth in a subsequent post.